Windows’ January 2022 Patch Tuesday update patches an elevated access bug
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
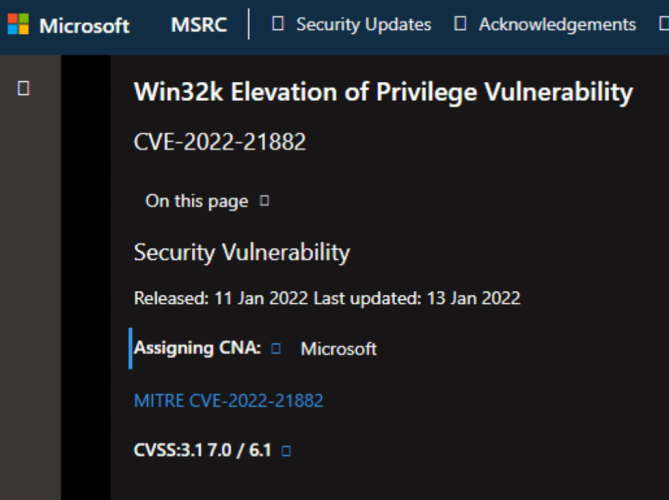
In a blog post by Bleeping Computer, a security researcher has published details of their exploit of a previously undiscovered local privilege elevation vulnerability in Windows 10, which allows any user to gain administrator privileges on the operating system.
CVE-2022-21882, a vulnerability in Windows 10 allows threat actors with limited access to a compromised device to easily elevate their privileges and perform privileged commands, allowing them to spread laterally within the network and create new administrative users. The vulnerability is a means of exploiting CVE-2021-1732, the previously patched bug.
William Dormann, a vulnerability analyst for CERT/CC, tweeted that he had demonstrated that the exploit worked and provided elevated privileges. BleepingComputer was able to independently verify the vulnerability’s existence, but could only get the exploit to work on Windows 10.
As the bug has already been patched, most PCs are not affected by it. However, some admins chose to skip the January 2022 Patch Tuesday updates because of the collection of critical bugs. As a result, some PCs remain susceptible to the recently-fixed vulnerability.
This means that they are at risk of compromise by a known exploit used in cyberattacks by advanced persistent threat (APT) groups. Microsoft has released out-of-band updates to fix vulnerabilities in the January 2022 updates. the elevated access bug. Administrators are advised to install the updates immediately.