Microsoft disables the MSIX ms-appinstaller protocol handler to help stop the spread of malware
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more

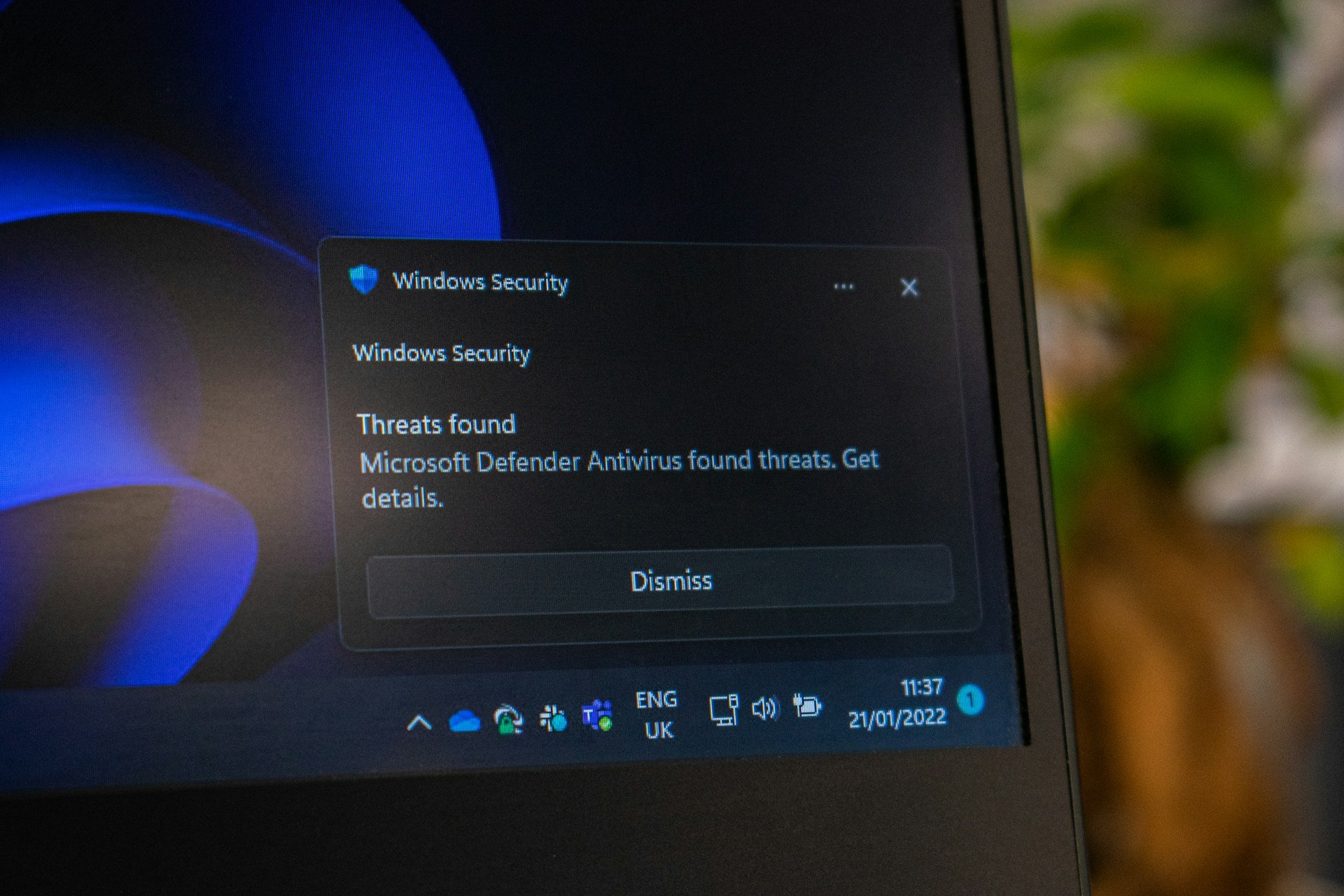
Microsoft recently announced that it has disabled the MSIX ms-appinstaller protocol handler to help stop the spread of viruses and other common threats that target Windows users. The change mainly impacts developers who might list MSIX files on their websites and addresses a Windows vulnerability first raised by Microsoft in December of 2021.
For those unfamiliar, the MSIX ms-appinstaller protocol handler is a Windows feature that was intended to allow users to install a Windows app without having to download an entire MSIX package. It was in use by many developers so that folks could install an app directly from a web server, but those with bad intent were also using the feature to their advantage. As an example, Microsoft indicated the AppX installer was being spoofed to inject malware like Emotet, Trickbot, and Bazaloader.
Microsoft is actively working to address the issue, and the first part of that involves disabling the feature. For a bigger solution down the line, Microsoft is looking into creating a Group Policy so that IT admins can re-enable the protocol and control the usage of it within their organization.
As a workaround in the meantime, users will need to first download these kinds of MSIX apps to their device, and then install the package with App Installer. The one caveat to this, though, is that the download size for packages might be increased. Microsoft also recommends that developers update the link to an application by removing ‘ms-appinstaller:?source=’ so that the MSIX package or App Installer file will be downloaded to an end user’s machine.