Latest Google Chrome release addresses zero-day vulnerabilities for Windows users
2 min. read
Published on
Read our disclosure page to find out how can you help Windows Report sustain the editorial team Read more
Google Chrome just got bumped up to 103.0.5060.114. This version is in place to help Windows users bypass a zero-day vulnerability, which hackers use to compromise their system. As spotted by the folks at BleepingComputer, this marks the fourth Chrome zero-day patch update this year.
The zero-day bug fixed today (tracked as CVE-2022-2294) is a high severity heap-based buffer overflow weakness in the WebRTC (Web Real-Time Communications) component, reported by Jan Vojtesek of the Avast Threat Intelligence team on Friday, July 1.
According to a blog post by Google, they confirmed that they were aware of the CVE-2022-2294 exploit. The latest version has already hit general availability worldwide in the Stable Desktop channel. They further indicated that it would only take a couple of days or weeks till it was available across the entire userbase.
Google has indicated that the attacks via this threat “range from program crashes and arbitrary code execution to bypassing security solutions if code execution is achieved during the attack”. However, they are yet to provide a detailed account highlighting any of these attacks.
That said, Google has stated that “Access to bug details and links may be kept restricted until a majority of users are updated with a fix. We will also retain restrictions if the bug exists in a third-party library that other projects similarly depend on, but haven’t yet fixed.”
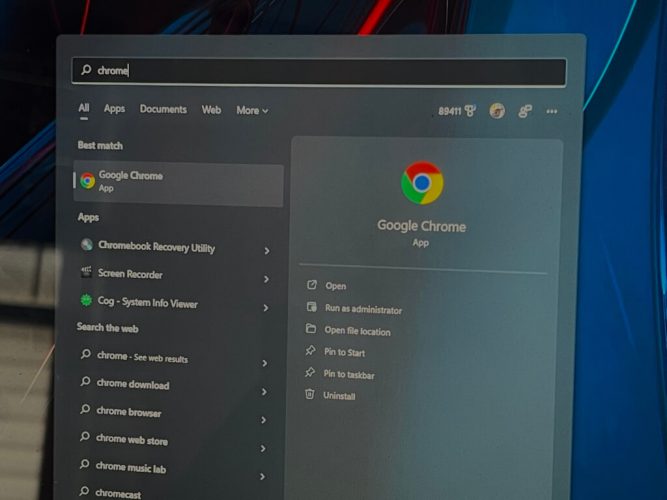
For Windows users, your browser is supposed to automatically install this update, but if this is not the case then you can go to your browser’s menu, then click on Help and select About Google Chrome to manually update it.